The move to cloud applications is a significant displacement in the field of software development that changes not only how companies manage and secure their data, but how they keep business applications up-to-date and scalable as well. The move to the cloud creates a new type of threat- cyberattacks, stressing the significance of secure applications development in the cloud. What is most important is that developers, business owners, or technology enthusiasts should make security in cloud applications their priority. With the escalation of cyber threats, the need for individuals to develop cyber defense skills and acquire tools is no longer just a matter of being aware, but it is a necessity. For comprehensive instructions on building secure cloud apps and to get details on how to do that easily and effortlessly, be sure to check syndicode.com/blog/cloud-application-development/. This resource is developed to guide you in building the security of your cloud applications against potential known problems.
Core Principles of Secure Application Development
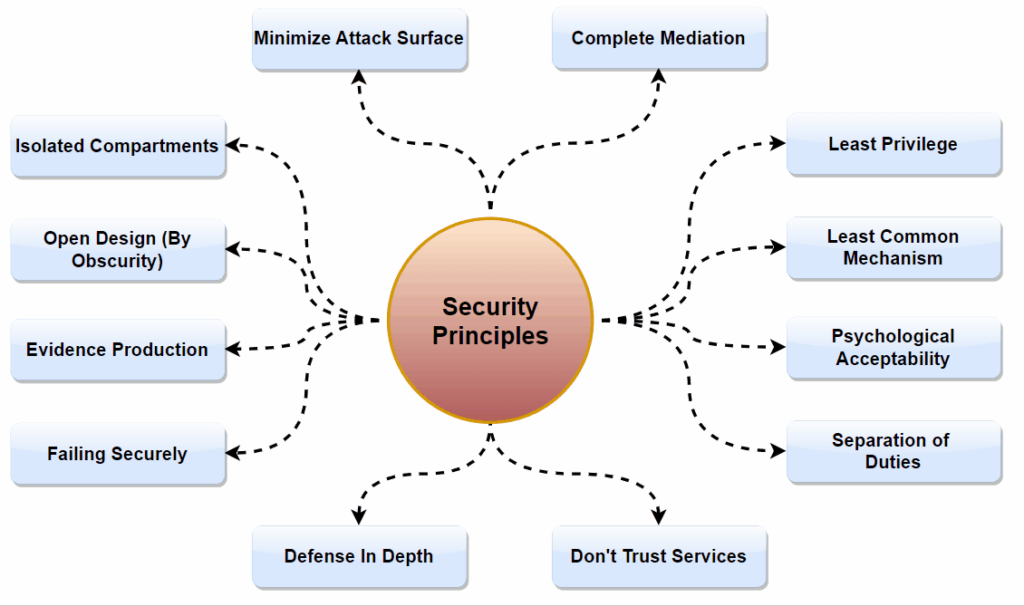
Developing applications with a good base in some core principles rather than a pure-driven approach will have the highest security. These principles are not just theoretical ideals but foundations upon which secure applications are built:
- It is paramount that security is integrated into the application design from the start as a main element, not as an appendage.
- Establishing security control and standards is a guideline for implementing secure applications.
- AI can be regarded as one of the key factors in ensuring the security of the systems by detecting and responding to any real-time attacks.
To encapsulate the essence of secure cloud application development, consider these guiding principles:
- Security should be given consideration right at the outset and security needs should be incorporated in every development phase.
- Follow industry best practices and standards. Do not forget to update security standards accordingly.
- Make use of AI technologies to augment the security features of your platform app by ensuring it can trace and respond to threats.
Crucial Techniques for Developing Safe Applications
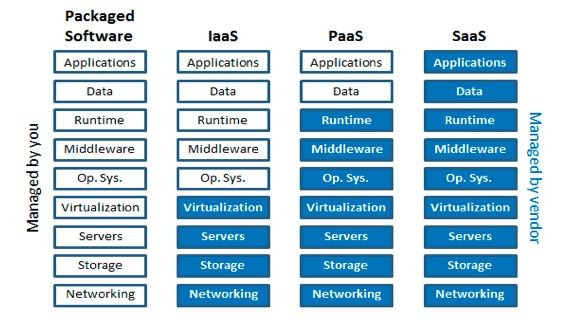
The features security and dependability capabilities that the cloud service provider provides are the foundation for the security of cloud applications. It is crucial to identify security measures, ensure that service providers are reputable, and comply with industry requirements. The kind of security measures that are employed, such as data encryption, frequent security audits, and a strong infrastructure designed to withstand assaults, should be one of your top priorities.
Embedding Security Throughout the Development Process
DevSecOps as a process means security is never assumed to be a done job, it remains a constant concern all through the application development lifecycle. Here, security tools and practices used within the development lifecycle, such as testing and maintenance, are incorporated in the earliest stages. It facilitates the coordination of a set of teams that comprise developers, operations, and security, towards an overall objective of risk management.
Ensuring Data Security
Data that is held in cloud applications is usually of the highest value, which is why its protection is the top priority. Key practices include:
- Encoding data not only at rest but also during transmission to ensure that access by unauthorized parties is excluded.
- Carrying out stringent access controllability to limit people who can access sensitive information should be done.
- Security and regulatory compliance are the priority, look for storage solutions that offer high levels of security and compliance.
Establishing Strong Authentication and Authorization Mechanisms
Strong authentication and authorization mechanisms not only protect the information from unauthorized access but also play a key role in this regard. There we shall adopt multi-factor authentication, use role-based access controls, and constantly watch out for strange access patterns that may be indicative of a breach.
Ongoing Security Evaluations and Compliance
The security operations of cloud apps now include ongoing security evaluations and compliance checks. This includes conducting penetration testing, and vulnerability assessments, and ensuring that the application code complies with all applicable laws and regulations.
Enhancing Cloud Application Security
Once the foundational strategies for building secure cloud applications are in place, it’s time to look at advanced methods to further bolster your defenses. Implementing these can set your application apart in terms of security and reliability:
- Encryption should not be limited to data at rest or in transit. Consider encrypting your entire application stack where feasible. This approach makes unauthorized access significantly more difficult for attackers.
- AI and machine learning can be game-changers in detecting unusual patterns that may indicate a security threat. These technologies can automate the detection of anomalies in real time, providing an additional layer of security.
- Zero Trust is a security model that assumes breach and verifies each request as if it originates from an open network. Implementing this model can minimize the impact of a breach.
- Engaging in regular penetration testing by ethical hackers can uncover vulnerabilities before attackers do. This proactive measure is crucial in maintaining a strong security posture.
- With regulations constantly evolving, continuous compliance monitoring ensures your application meets the latest standards, avoiding potential legal complications.
A Proactive Stance on Security
The most important thing to do when it comes to cloud application security is not a matter of using the right technologies only but it is also about building a security-conscious culture in your organization. This final tip may seem straightforward, but it’s often overlooked: frequently you need to patch up your software and also update it. Apart from new features, software updates also encompass security patches for recognized weak points. A conscious disregard of updates in your software will leave it vulnerable to well-known risks and easily abused by an attacker.
At the endpoint, keep in mind that security protection of cloud apps is a continuous process, not a once-off job. With technology evolution, the occurrence of cyber threats is increasing as well. To be effective, keeping security is the best, staying alert and proactive will certainly help. Your work in establishing cloud applications not only makes your business safer but also helps the internet to be safer. Let this be a call to action: place security as a top priority, implement the cutting edge of protective measures, and, most importantly, keep one step ahead of the enemies.


