Most individuals and organizations take safety measures online to deal with phishing, ransomware, etc. but taking care of physical security is also vital. Fraudsters are utilizing tailgating attacks to gain physical access in protected or unauthorized areas. They use deception, kindness, etc. to follow people inside secure places without any passwords or raising alarms.
A report states that the global market for tailgating detection systems will reach around $100 Million by 2028. More and more organizations are now vulnerable to such attacks where criminals take advantage of unsuspecting and helpful employees. With the use of artificial intelligence in cybersecurity, we need to detect and stop tailgating attempts. Further we’ll know more about these attacks along with some cybersecurity and other safety measures to stay safe from them.
How Does a Tailgating Attack Work?
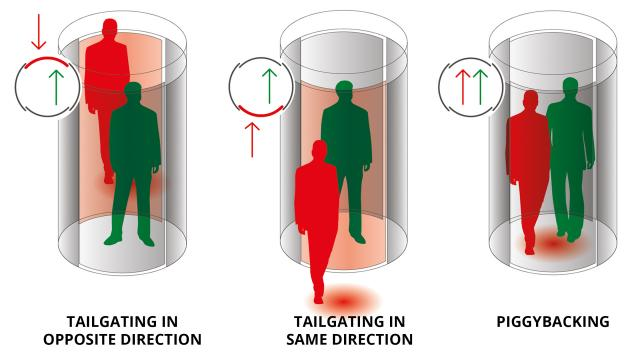
When a scammer or any unauthorized person follows an unsuspecting employee with legitimate access to enter into restricted or protected areas, it is referred to as a tailgating attack. It is a combination of social behavior and technology, exploiting both physical and digital security measures. The attacker will pose as a vendor, delivery person, etc. delivering various supplies, parcels, food, or anything else.
He will ask an employee to hold the door for him as his hands are full and enter the area like this. Some attackers also ask for employees’ phones claiming that their phone has switched off and install malware or steal personal data.
Their main purpose is to gain trust and then launch an elaborate attack. Attackers can connect to official networks or place devices that can ruin the systems soon. This makes it important for organizations to improve their cybersecurity and physical security both.
Common Methods Used for Tailgating
Over the past 2 years, social engineering attacks have gone up by almost 270%, and criminals are getting creative with their tailgating techniques. Thus, employees should never hesitate asking for cyber security help if they notice anything fishy. Here are some common methods used by them.

Acting as a Friendly Stranger
Usually, the attacker will wait near the door and start a casual talk with any employee that has access. They act like a new joining, pretend to forget their ID card, or act as if their hands are full. The employee opens the door and lets them inside.
Fraud Delivery Boy
Another common tactic is to pose as a delivery boy. They come holding many parcels or heavy packages so that employees quickly open the door without any confirmation of identity check.
Impersonating Someone
In this case, the attacker will pretend to be from the IT staff, requiring immediate access to restricted or password-protected areas, to fix technical issues. It is possible that an unsuspecting worker allows them to enter. This makes measures like authentication using CAPTCHA and similar protocols important to prevent unauthorized access.
Attacking After Regular Hours
Organizations are less vigilant towards tailgating attacks during night shifts or when the regular working hours are done with. Attackers try to follow night-shift employees inside the building claiming that they forgot their stuff inside in the morning.
Which Organizations Have High Risk of Tailgating Attacks?
Many people tighten their security online, but don’t focus much on the physical aspect. They believe cyber criminals won’t take the physical route but they are wrong. The following organizations are at high risk of suffering a tailgating attack and must utilize cyber security help –
- Organizations that have lots of employees moving in and out of the building.
- Large buildings with multiple points for entry as well as exit.
- Organizations that regularly receive deliveries like parcels, packages, food, documents, etc.
- Companies with many third-party vendors and subcontractors working along with them.
- Companies that don’t provide proper cybersecurity and physical security training to workers.
How to Tackle Tailgating Attacks – How Cybersecurity Helps
Over 70% of organizations consider themselves vulnerable to tailgating, but just 15% of them track incidents regularly. They can take the following digital and physical measures to minimize the risk of tailgating –
Better Employee Training & Awareness
Companies need to prioritize training their employees about social engineering attacks like tailgating so they can identify and take action accordingly.
Smart ID Cards & Badges
Use smart badges and cards to gain access to restricted areas. Also, such cards make sure that employees can identify each other and not allow outsiders inside.
Biometric Scanning
It is an advanced way to authenticate the ID of an employee. Common methods include voice recognition, facial recognition, fingerprint sensors, etc.

Strict Access Control
Use access control systems in which everyone needs to authenticate individually to enter. This is really helpful in reducing tailgating.
Regular Audits & Security Checks
An organization should conduct audits and security checks regularly. This helps know vulnerable areas and improve security wherever it is needed.
Tailgate Detection System
You can get advanced tailgating detection systems that feature alarms and sensors to notify if a person is following someone, or has entered a restricted area.
Conclusion
Social engineering attacks like tailgating are on the rise, and organizations must have a proactive and vigilant approach to fight them.
We talked about how criminals use this attack and how you can stay safe. Make sure to utilize artificial intelligence in cybersecurity along with other digital and physical measures to minimize tailgating threats.
Meta Description: Guard against physical security breaches like tailgating attacks. Learn how AI in cybersecurity can prevent unauthorized access. Stay safe online & offline.
Strengthen Your Online Privacy and Infrastructure Security
Ready to take your cybersecurity to the next level?
Consider enrolling in Tesseract Academy’s GDPR, Data Privacy, and Cybersecurity course for Small Businesses. This comprehensive program equips you with essential strategies for fortifying your defense against online threats.
ENROLL NOW and fortify your defenses against cyber threats!

