The growing presence of cybercrime poses a notable threat to national security, reputable entities, and influential government organizations in terms of engaging ethical hackers.
Although hacking is linked with illegal activities, it is important to identify that not all hackers are engaging in malicious actions. There are a few hackers who use their skills to breach the security systems of companies, extracting important details against the law.
However, the real essence of hacking is still a mystery to several individuals. Ethical hackers, also known as white hat hackers, are employed to identify the risks within a system and implement proper risk management programs, such as third—and fourth party risk management.
What Is Ethical Hacking?
Hacking often raises major concerns related to theft and crimes. However, ethical hacking, also known as white hat hacking, is the method used by ethical hackers to infiltrate a network, application, or computer system on behalf of a company with their consent. Unlike hackers, ethical hackers do not intend to disrupt businesses; instead, they test the strength of security.
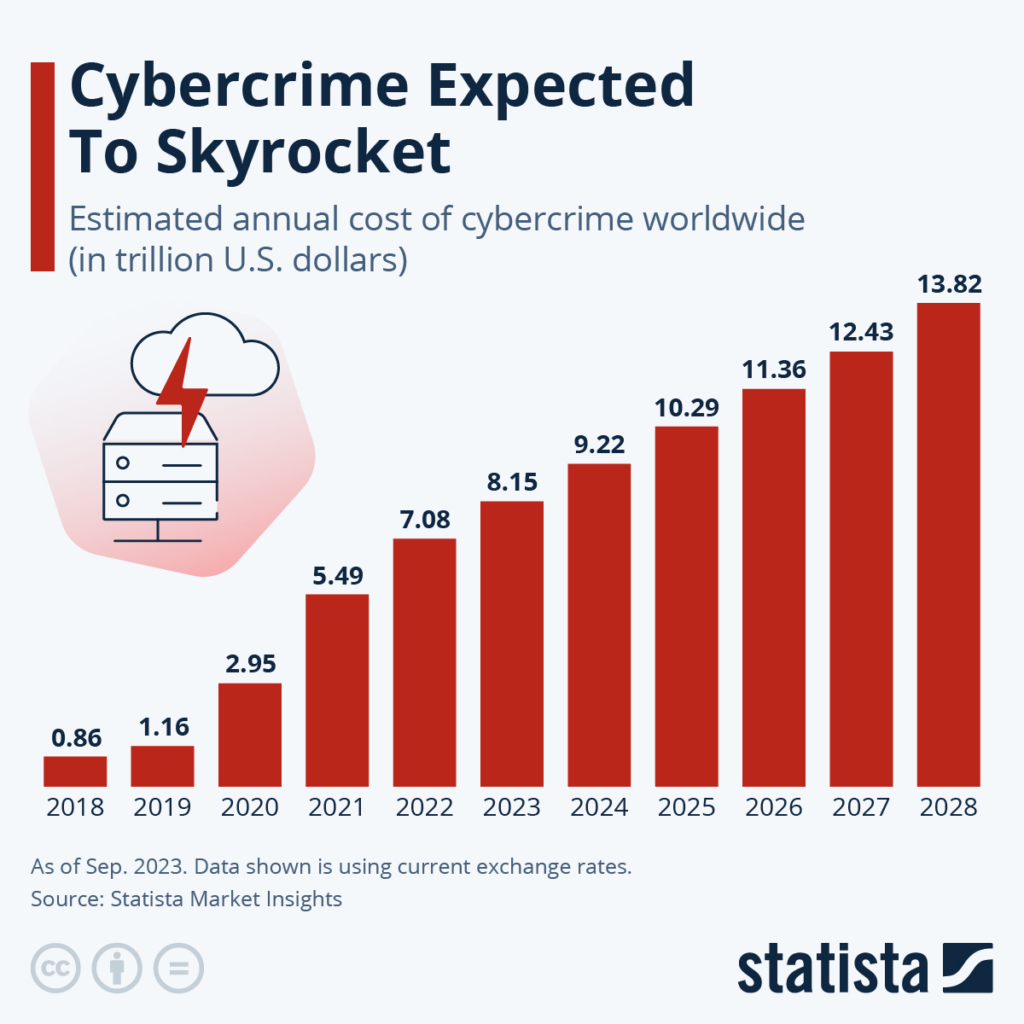
Statista’s Market Insights has reported that the global cost of cybercrime is expected to surge in the next four years, rising from $9.22 trillion in 2024 to $13.82 trillion by 2028.
Ethical hackers use the same methods for infiltrating the network as their unethical allies. However, they need not have malicious intent to exploit risks or disrupt the business. They will document every risk, leveraging threat intelligence to equip companies with better threat solutions and strategies.
Vulnerability Assessments and Penetration Testing
Risk or vulnerability assessments normally involve the systematic review of the system of the company, networks, and applications that identify the possible weaknesses that get exploited by hackers. The regular conduct of vendor risk assessment can help a business to remain ahead of the game, addressing the possible risks before they get exploited.
Alternatively, penetration testing will be an add-on step for risk assessment. It involves simulating real-world hacking attempts that uncover the risks that were missed during the initial assessment phase. The penetration testers, also considered ethical hackers, will use numerous tactics and tools to exploit weaknesses and attain unauthorized access to these systems. The process will allow companies to identify possible entry points, validating the potential of these security measures.
The benefits of risk assessments and penetration testing are never overstated. They offer key insights into the company’s security posture and help uncover weaknesses that could lead to data breaches and other security incidents. Identifying and addressing risks proactively can help businesses strengthen their cybersecurity defenses and reduce the risk of falling into the hands of malicious attacks.
Additionally, risk assessments and penetration testing play a vital role in compliance with industry regulations and standards. Several regulatory frameworks will require the company to regularly assess its security controls while demonstrating its commitment to maintaining a secure network for its stakeholders and customers.
How Ethical Hacking Improves Security and Prevents Cyber Attacks?
The rising cybercrime has made it important for businesses to use every technique to build their active defenses. These days, ethical hacking and cyber security are important to safeguard the corporate computer systems and networks that will place white hackers in growing demand.
White hacking is the ideal way to help companies place their security to test without any possible risk. The ethical hackers will help the companies find holes in their security and advice how to change every internal process to tighten up things. Let us check out the primary phases involved with the hacking process.

Reconnaissance
It is the first step in hacking and is also considered the footprinting phase. It is the preparatory phase where the hackers gather information about the target to detect its weaknesses. In this process of surveillance, the hackers mainly collect information about three groups: the network, people, and the host involved. Active and passive reconnaissance are the two forms of Reconnaissance.
Active reconnaissance indicates direct interaction with the target for gathering information, such as using tools for scanning the target. Passive reconnaissance is all about gathering information about the target without accessing it directly. It consists of data collection from public websites, social media, and more.
Scanning
The hackers will use various methods for probing and scanning the defenses of the company. There are normally three forms of scanning available:
- Port Scanning involves scanning for information like live systems, open ports, and numerous services operating on the host.
- Vulnerability scanning is checking the target for the risks or weaknesses that get exploited.
- Network mapping indicates the discovery of the topology network of networks, firewall servers, or any host information. Since then, the hackers will create a network diagram with the information available.
Gaining Access
During this point, a hacker has the information that he needs on zero trust network access. The phase involves the attacker breaking into the system or network using numerous methods and tools.
Initially, he needs to decide on how to carry out the attack. There are numerous options, such as brute force attacks, phishing attacks, session hijacking, spoofing attacks, and more.
After gaining access to the system, the hacker increases his ability to administrate ways to install a much-needed application for hiding or modifying the data.
Maintaining Access
After having access, the hacker will retain the access for exploiting data in the future and possible attacks. The hacker will also secure access to the trojans and rootkits, using them to launch more attacks across the network.
An ethical hacker will help to try to maintain access to the target till he is done with the tasks that he planned on accomplishing the target.
Optimization
A sound hacker is always clear about the evidence so that one can find his traces later. This involves modifying, corrupting, and deleting value logs, modifying registry values, installing different applications used, and deleting the folders created.
Removal of the traces is an obligation that falls under the hacking craft. An ethical hack, when not done correctly, carries specific risks for the firm.
The only targets of ethical hacking are evaluating the strength of these security defenses, identifying risks, and undertaking measures to remediate them. Professional hackers do these with the qualifications to make businesses more prepared during a possible attack.
Conclusion
Ethical hacking has evolved as an important tool for protecting our digital world. The arduous effort of the white hat hackers contributes notably to strengthening the cyber defenses across the global industries. The continuous advancement of technology can protect valuable information assets from those in search of unauthorized access.
Author: Nagaraj Kuppuswamy is the Co-founder and CEO of Beaconer, an esteemed enterprise specializing in managed third-party risk using the cloud-native AI-based solution. With an extensive portfolio of accolades and industry certifications, Nagaraj stands out as a seasoned expert, boasting over 16 years of dedicated involvement in the field of Cybersecurity. Throughout their career, he has predominantly

Strengthen Your Online Privacy and Infrastructure Security
Ready to take your cybersecurity to the next level?
Consider enrolling in Tesseract Academy’s GDPR, Data Privacy, and Cybersecurity course for Small Businesses. This comprehensive program equips you with essential strategies for fortifying your defense against online threats.
ENROLL NOW and fortify your defenses against cyber threats!

